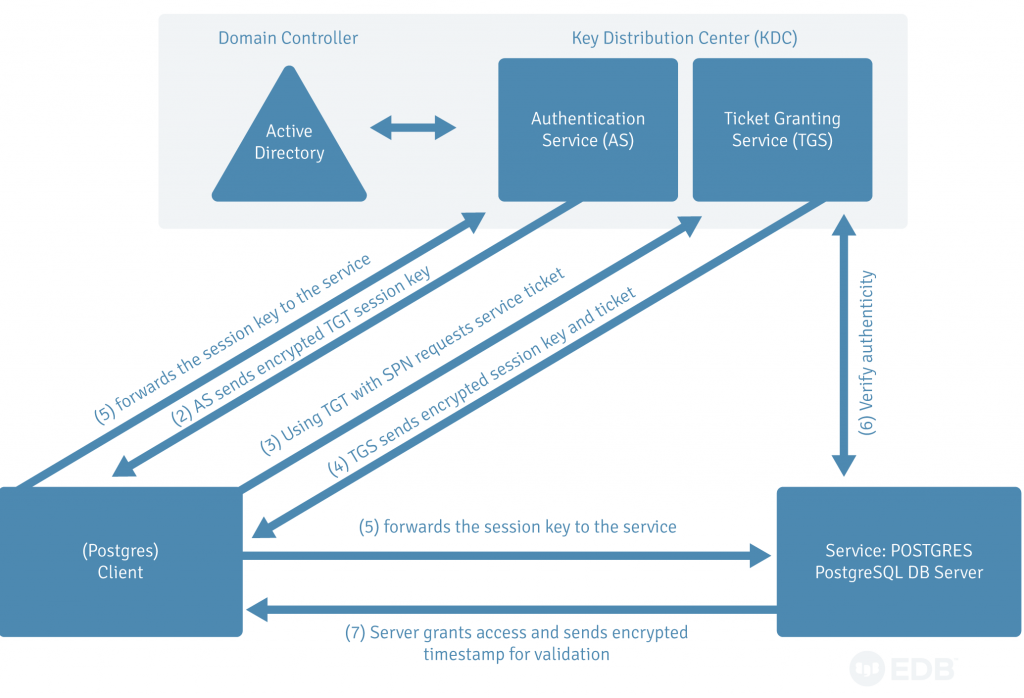
Autenticazione composta e attestazioni di Active Directory Domain Services in Active Directory Federation Services | Microsoft Learn
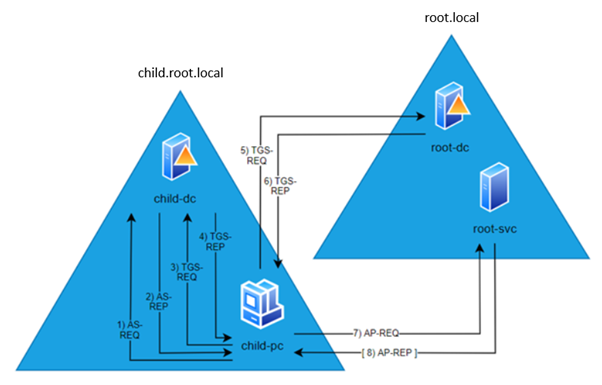
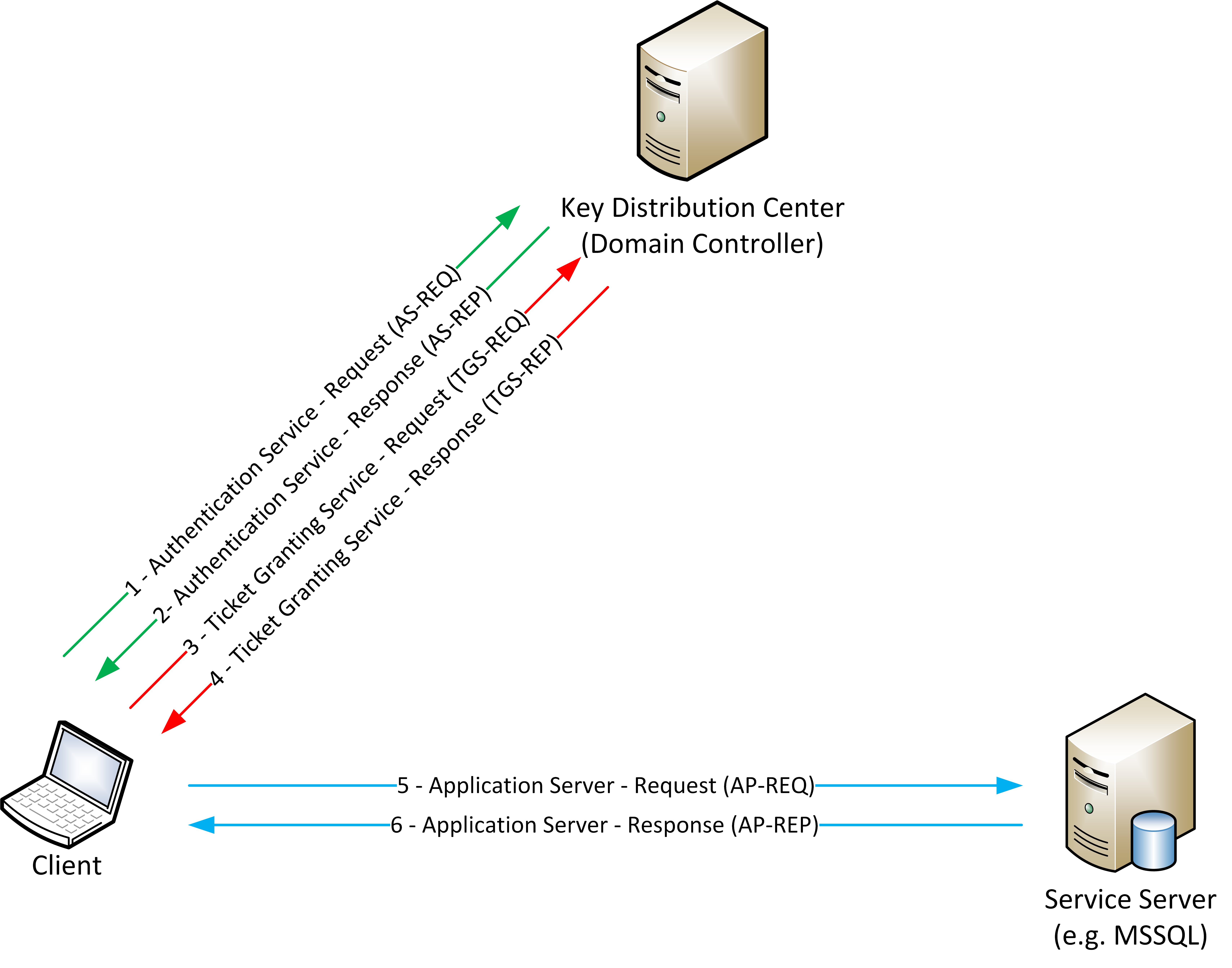
SID filter as security boundary between domains? (Part 1) - Kerberos authentication explained — Improsec | improving security
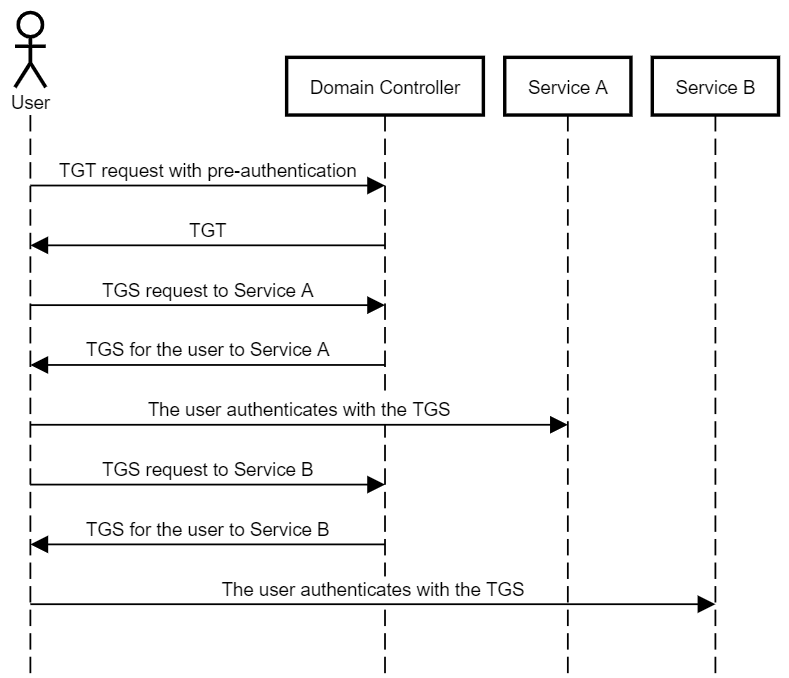





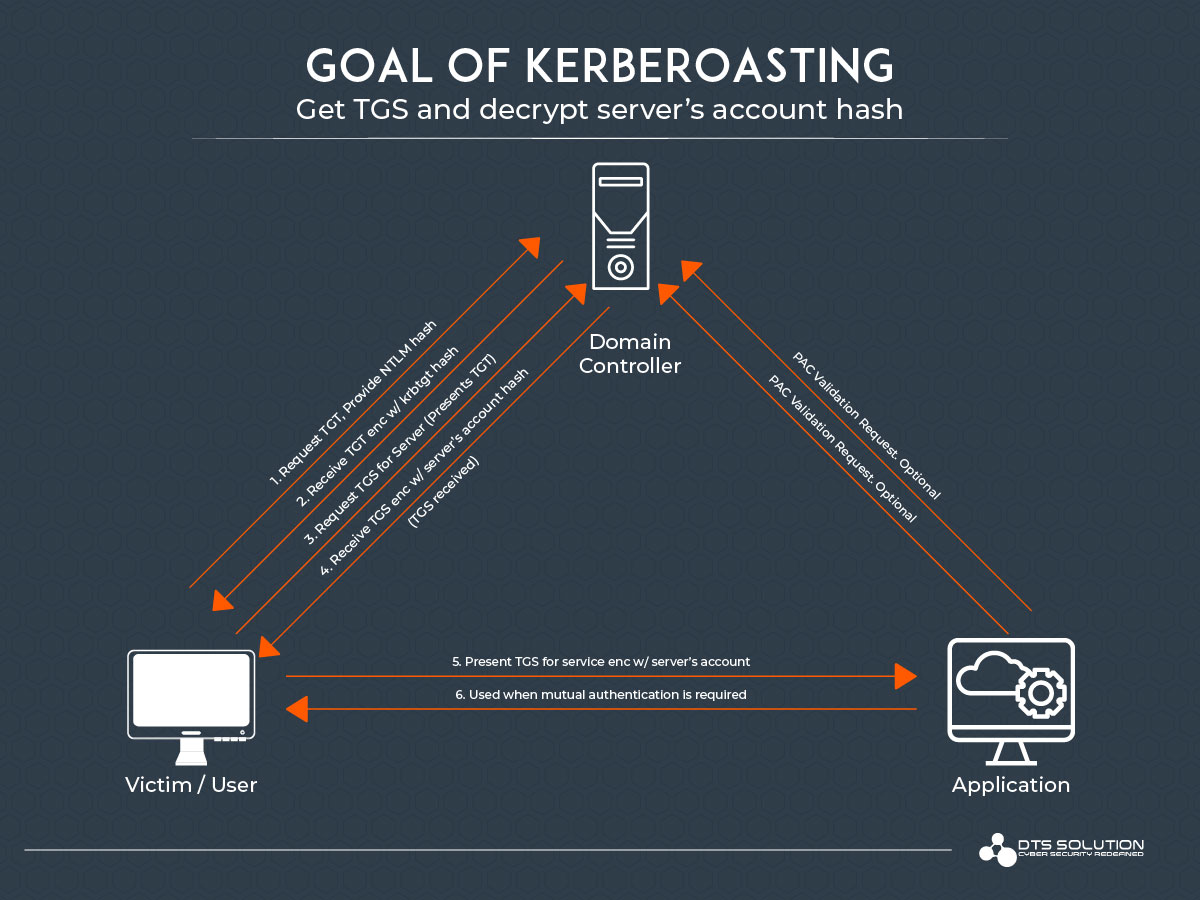

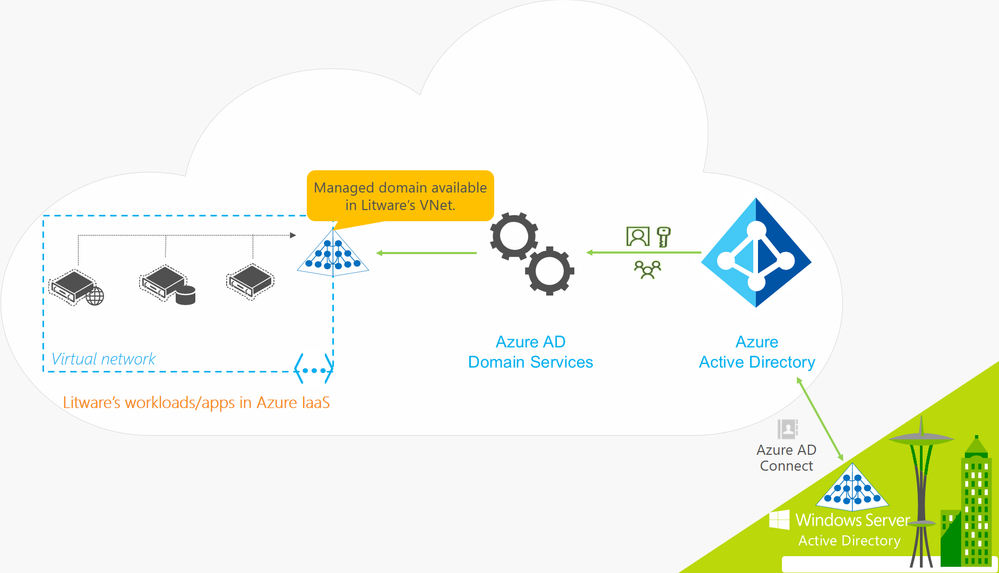
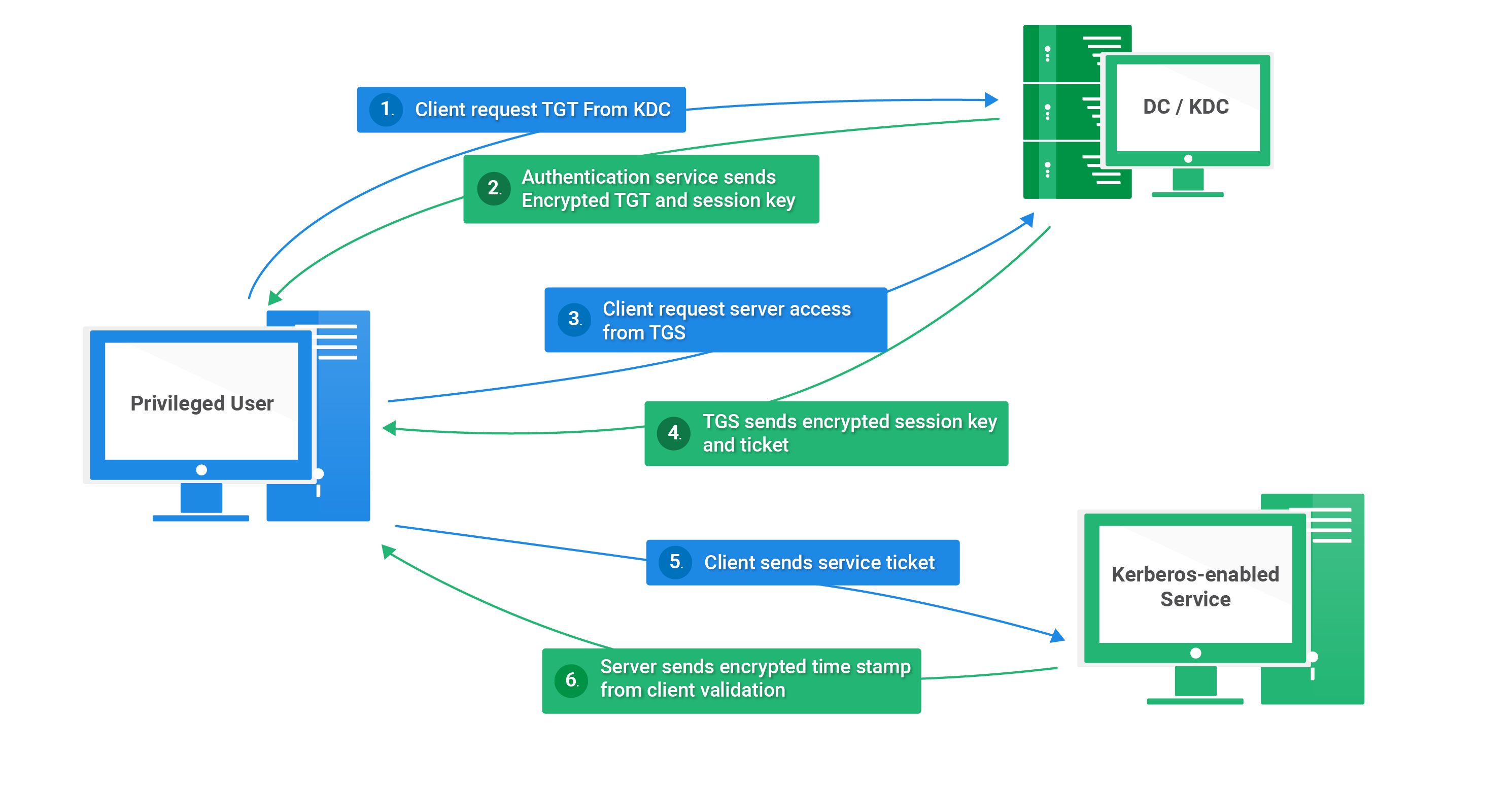
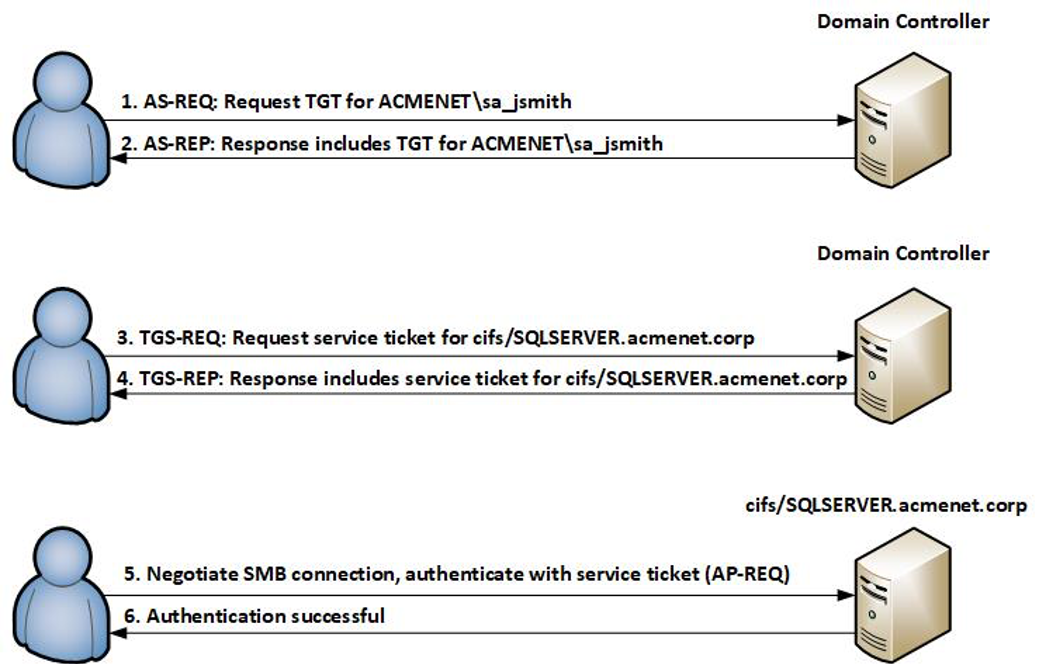
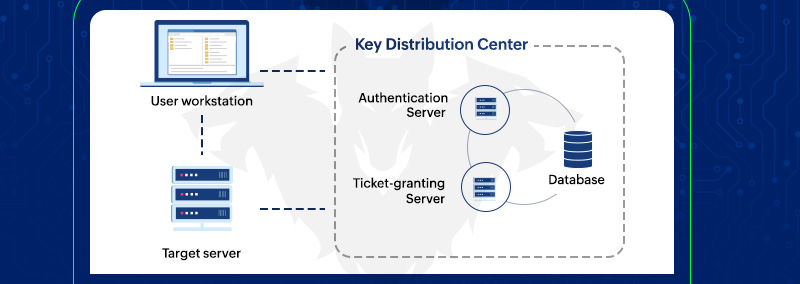
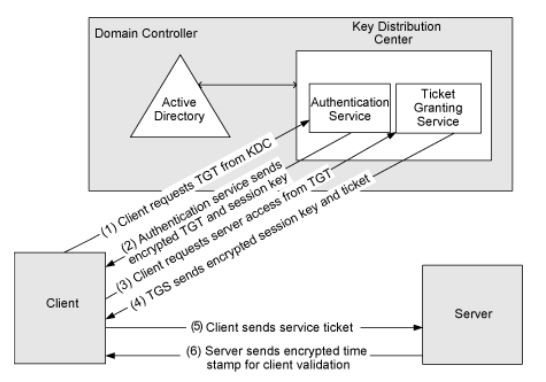
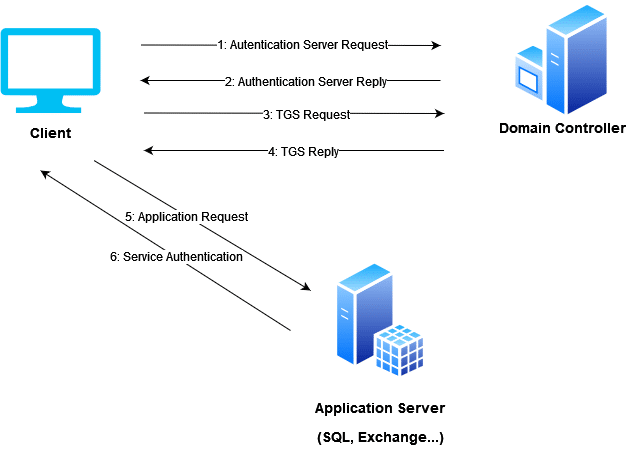
![Kerberos KRB_TGS_REP message [11] | Download Scientific Diagram Kerberos KRB_TGS_REP message [11] | Download Scientific Diagram](https://www.researchgate.net/publication/353593170/figure/fig5/AS:1051484670152706@1627704889837/Kerberos-KRB-TGS-REP-message-11.png)